[ad_1]
Google Chrome Extensions are super useful. You get to use them with other chromium-based browsers like Microsoft Edge. So, if you are a user of any of these browsers, know that most of these extensions not only collect a lot of data about you, your device, and your browsing habits, but also use the same to track your online activity and perhaps even serve personalized ads based on that. One of the methods involved in this data collection and tracking is called fingerprinting. Now, a recent report by web developer z0ccc (via Bleepingcomputer) has raised concerns of how Google Chrome extensions are intrusive in the way they fingerprint you.
Here’s everything you need to know about Fingerprinting by Chrome extensions.
Google Chrome Extensions Fingerprinting: What it means?

The Chrome Extensions are alleged to collect data about the user’s system like display resolution, installed applications and fonts on the computer, hardware configuration, and even performance stats.
Now these data are extracted to find which all cohorts the user falls in. The intersection of commonality between the various groups helps in triangulating the individual user.
Coming to the titular problem, which has suddenly garnered lots of attention is thanks to the web developer z0ccc’s website titled ‘Extension Fingerprints’ that can release a tracking hash by just scanning all the installed browser extensions. It relies on built-in browser extension properties like ‘web-accessible resources’ and ‘Resource timing comparison’.
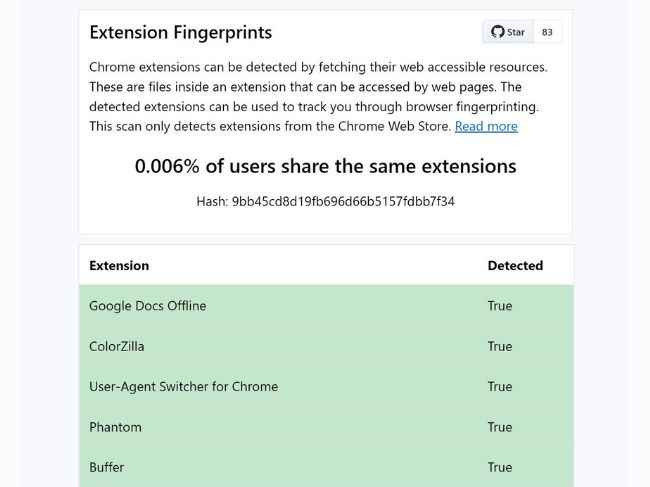
These properties are apparently present on 1,170 popular extensions including popular names like Grammarly, uBlock, LastPass, Adobe Acrobat, ColorZilla, Honey, and Rakuten.
The developer remarks that only extensions downloaded from Chrome Web Store are the cause of concern. Even though Microsoft Edge’s Extension Store can and does host some if not, most of these extensions. The only relief is that for fingerprinting to work, the IDs of these extension files need to be tweaked. Meanwhile, the Mozilla Firefox users need not worry in this case as the Firefox extension IDs keep on changing every browser instance and are not suited for extended tracking and fingerprinting. You can find more technicalities about z0ccc’s findings here.
As for other news, reviews, feature stories, buying guides, and everything else tech-related, keep reading Digit.in.
[ad_2]
Source link
